Class Setup: My learning tech stack - Learn for Free
Greg Heffner September 8, 2024

*** Disclaimers: This is for learning purposes only. I do NOT recommend you keep this docker image running all the time due to the loose security settings I used in a contained environment. I would also recommend you use a VPN when connecting to the internet. The account used is "root" and password is "password" and should be changed. There is a mount on my local machine at /home/ansible/mnt/kali and it is mounted to the container at /root/scripts/ IF you follow the same build please update the folder location of the local drive instead of /home/ansible/mnt/kali if you want to share files between devices***
In previous blogs I talked about how much I like TryHackMe.com. In this blog Im going to show you how I setup my Kali machine and what scripts I run when starting some of the Capture the Flag exercises. There are a couple of ways someone can utilize a a Kali machine. I have both a full VM running on a ESXi node and also a Kali docker image I have recently used and kinda like it. I would recommend Kali Purple if you want to use a VM on your own. In this write up I am going to highlight the Kali docker image I have built.
Setup:
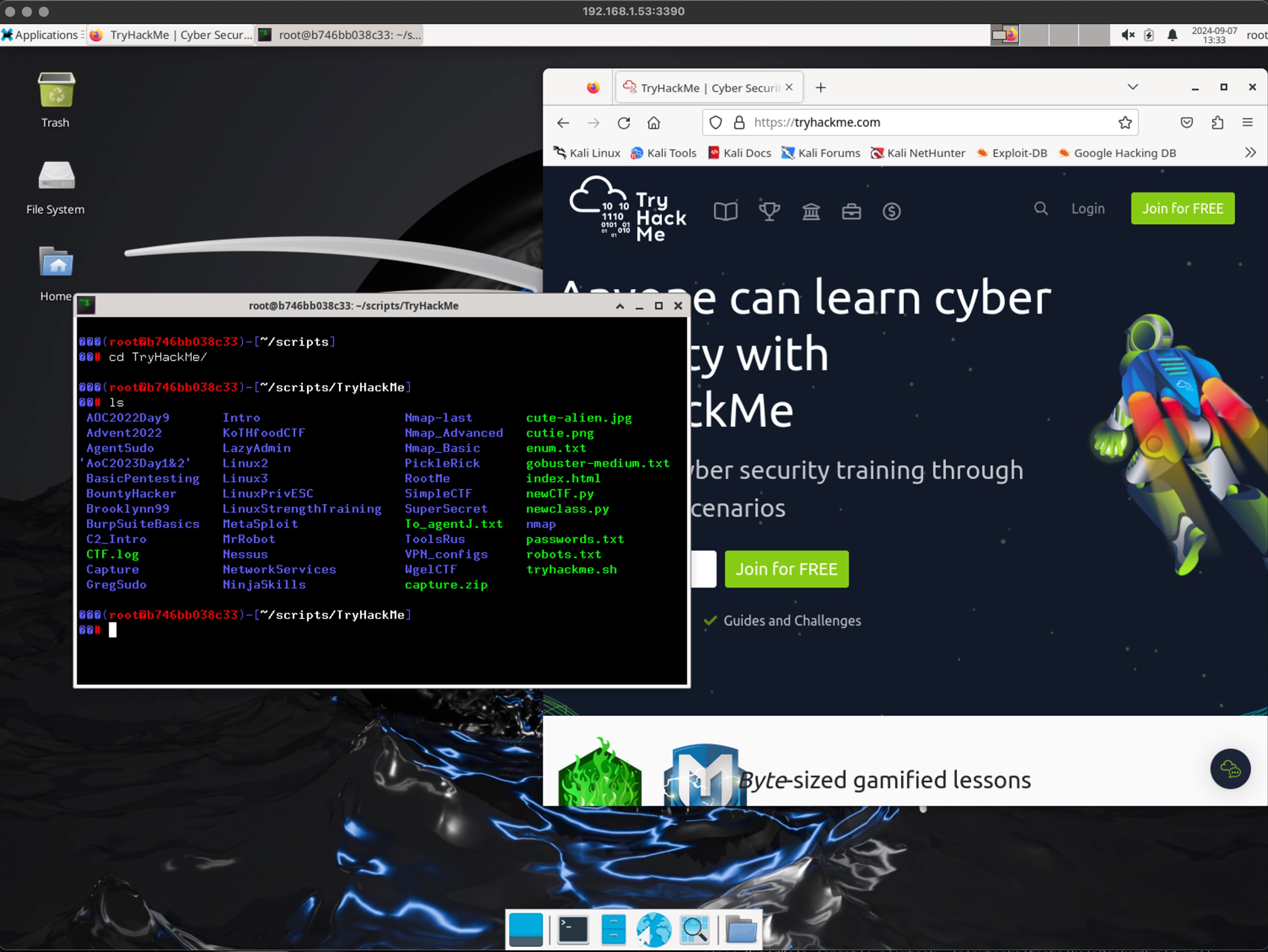
First I will say this image is HUGE. Like 30+ GB. The reason for this is I have the full package and all its contents included so no need for updates once downloaded. Here is the DockerHub repo with the image https://hub.docker.com/repositories/technotuba. I save all of my scripts locally in a file located in my /home/ansible/mnt directory. In this playbook I mount this location to the Kali Container for file storage.
I use a mixture of ansible tasks and bash aliases to setup my environment.
When I run the "BuildKali" alias as described in the readme file, this 'ansible-playbook ~/playbooks/tasks/kaliDockerBuild.yml' command is run on my local machine. This will pull down the kali full image, start and run the container, creates and starts a RDP service on port 3389. Once the playbook is done you will get a play recap and you should expect to see passing and updated changes. From here you can assume the container is running and jump right to trying to RDP to the IP address of the container but I would recommend you run "docker ps" to verify it is running and its port is being forwarded. Once you have verified open your favorite RDP application and log into the container with the IP and port number.
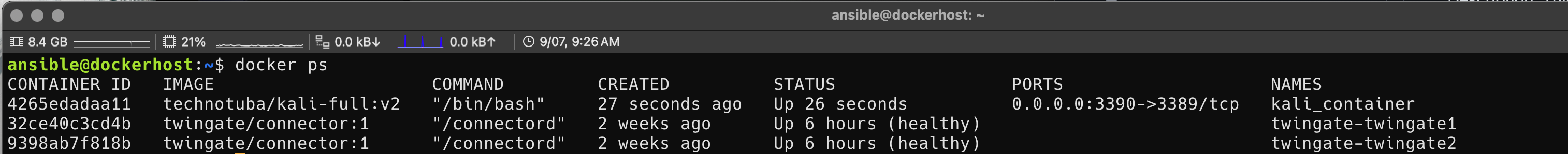
Open the browser at the bottom search bar and log into TryHackMe Access Page and download the machine config file for the server location closest to you. Open your terminal and run sudo openvpn "and then your config file name" to connect to the TryHackMe VPN. This will allow you to run commands locally from your machine in their labs.
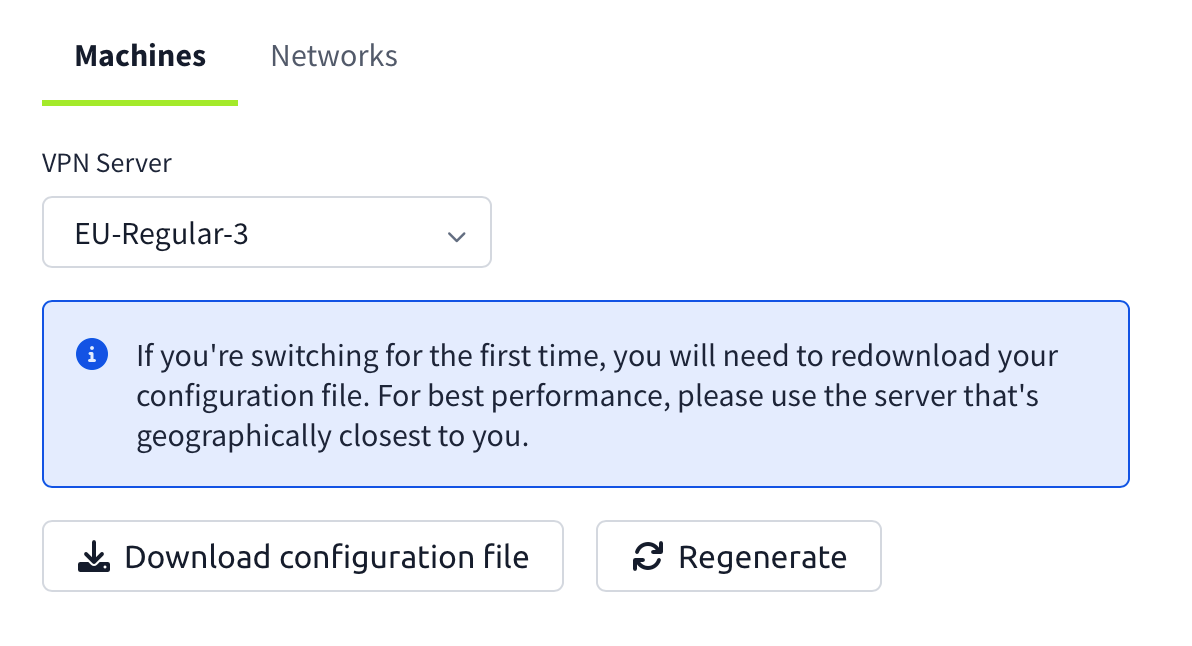
Course Selection and Starting:
In my Kali container, in my scripts folder, I have a TryHackMe folder I use to keep all of my school stuff together. This is where I clone the NewClass scripts that I run for each new class.
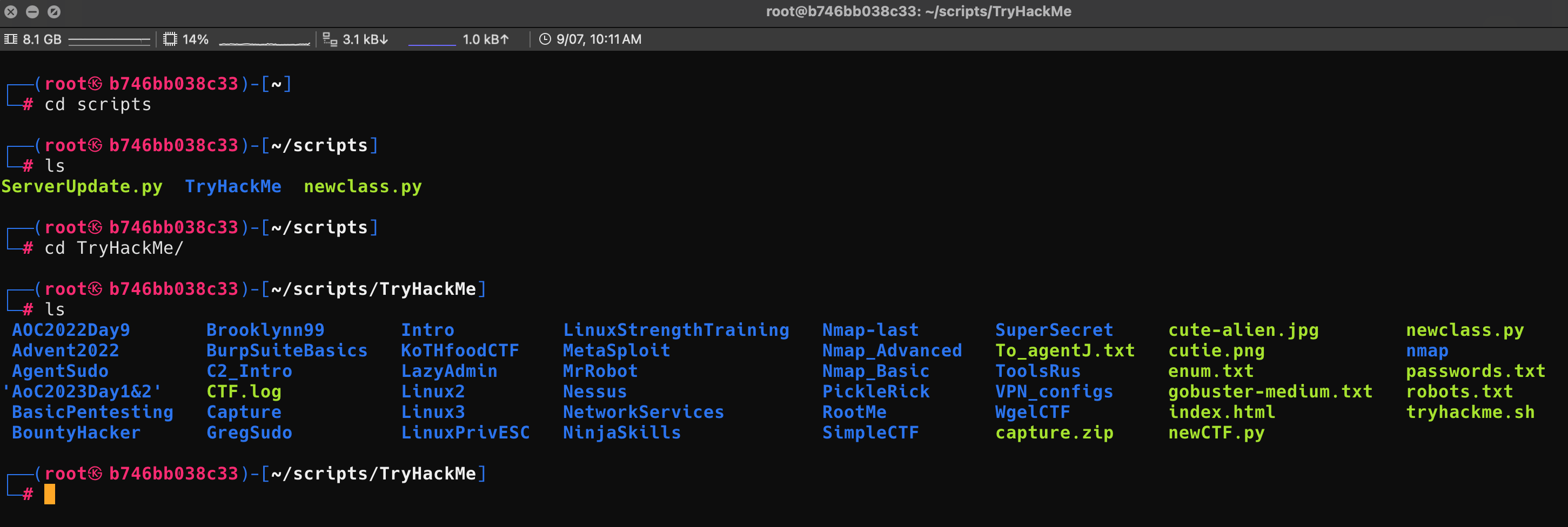
newclass.py
ip = input("Please enter an IP address: ")
className = input("Please enter the class name: ")
os.chdir("/home/kali/Documents/TryHackMe")
os.mkdir(className)
os.chdir(className)
# nmap scan the ip
os.system("nmap -sC -sV -Pn " + ip + " --stats-every 30s > nmap_results.txt")
# nikto scan the ip
os.system("nikto -h " + ip + " > nikto_results.txt")
This script asks you for the IP address of the machine you are trying to access, and the class name that you are taking. Once you put in those values a new folder with the class name will be created and you will be moved into that folder. A nmap and then a nikto scan is run against the IP that was given and their results are put into their corresponding text files. I found myself running these commands often enough to let them go each time. Feel free to edit and update with commands you like to run. Wanna learn more about those commands I run and why I run them. Join TryHackMe.com and check it out!
Completing:
Since the files and folders we created are inside a mount on our local machine, we can be sure that when we save and exit our work we can access it even if the container is not available. I close all of my windows and terminals making sure to close the OpenVpn connection to tryhackme. Once I have logged out of the RDP session I will go to my local terminal and run KillKali which will shutdown and close all connections and services related to my Kali container and stop the container itself.
Please leave some feedback in the Open Forum link either here or in the top right navigation bar link. Im trying to test ways to interact with my audience and give a place for feedback. I would LOVE to see some scripts you like to use when you do your own CTFs or training courses.
About Me
I served in the U.S. Army, specializing in Network Switching Systems and was attached to a Patriot Missile System Battalion. After my deployment and Honorable discharge, I went to college in Jacksonville, FL for Computer Science. I have two beautiful and very intelligent daughters. I have more than 20 years professional IT experience. This page is made to learn and have fun. If its messed up, let me know. Im still learning :)