VPNs: Web browsing and IP masking
Greg Heffner July 21, 2024

In todays age online security starts with a VPN
In order to get to a webpage most people will connect from their computer or cell phone, through the wifi, to a webpage online. In previous articles I talked about Pi-Hole and how a DNS server translated a web address like greg.heffner.live to an IP address like 104.21.46.194. This address is specific to this webpage. Think of this address like a calling card for how to get ahold of you anywhere in the World.
DNS Explained in 100 Seconds for a quick catch upA Virtual Private Network or VPN connection is a connection that allows you to browse the web from an address that isnt your personal IP address. When you go online whether youre on your phone, computer, tablet, car, watch, anything... your device has to share certain information with the devices you are interacting with in order to provide you with the best experience. Maybe you carry a cell phone because it easier than a tablet but as you know the screen size on a phone is smaller than your tablet. Maybe your computer uses chrome browser while your cell phone uses firefox browser. Each of these applications and devices have a different way they like to get information. When you use these devices online they have to tell the remote device they are interacting with a lot of details in order for it to know how to interact with the specific instance of your session. Why is this important you ask? This information is very specific to you.
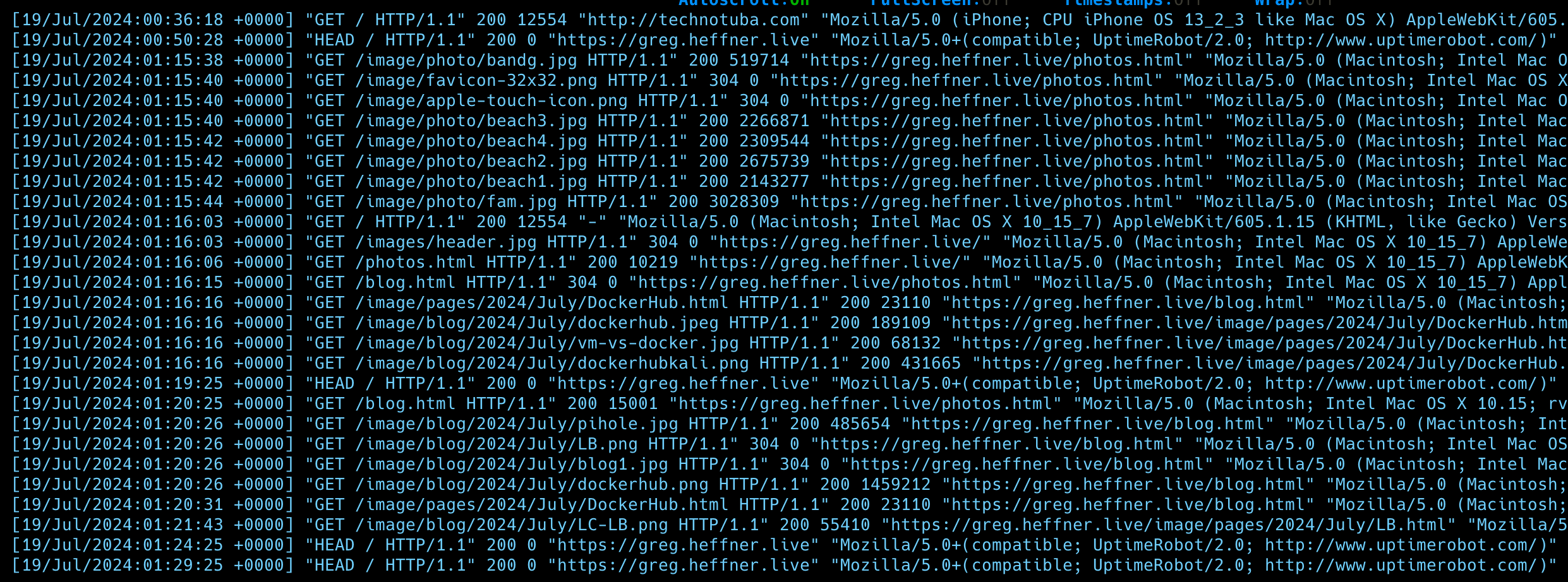
What is sent over the internet to load a webpage?
I opened my mac, opened chrome, and loaded the DockerHub Blog. When I loaded the page here is what was sent to my server and stored in the logs: [18/Jul/2024:01:19:17 +0000] "GET /image/pages/2024/July/DockerHub.html HTTP/1.1" 200 "https://greg.heffner.live/blog.html" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36" "104.21.46.194"
Lets break down what my device sent over the internet to load the page
-
[18/Jul/2024:01:19:17 +0000] - timestamp of the request
-
"GET /image/pages/2024/July/DockerHub.html" - The request type, in this case a GET request to download the DockerHub.html webpage
-
200 - A status code showing, in this case 200, that the response was successfully processed and the server sent back the requested resource
-
"https://greg.heffner.live/blog.html" - The reffering address or who sent you the info
-
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36" - User Agent - Provides info about the users browser and operating system. macOS 10.15.7 & Chrome version 126.0.0.0 in this example but each persons user agent will be different
-
"104.21.46.194" - The IP address the request came from
As you can see there is quite a bit of information sent over just to view a webpage.
What Does this Mean
This means everywhere you go online, every webpage, social media page, video streaming service, anything; will log when you go there, what device you used to go there, and who you are. All of this information is then stored and saved to become a digital fingerprint for all the traffic that comes from that IP address. Think of the type of information that could be gathered. Imagine someone knowing your habits. You wake up at a certain time and browse the web or check emails. You go to bed at a certain time. Your device location is probably at home, or it is in a hotel for a work trip. All this can be found from your IP and device info from traffic logs.
Cloudflare Radar is a great tool to see traffic patterns and where traffic is coming from.Depending on the information someone has of your traffic, you can generate different assumptions. Lets say someone has a way they can steal your credit card info if you use a certain type of web browser. Just search the server logs for the browser type youre looking for and bam, there is also a list of IP addresses that are vulnerable right next to your browser data. What if someone whats to steal your credit card information and know you shop online after work every payday and all weekend after. Almost like they found what you were allergic to, where you live, and when you usually get home.
This logging happens everywhere and most of the time it is for good reason. Businesses and companies log data like this to give their customers a better experience and for site analytics. If a company knows you always look for Taylor Swift music on the weekends, it might give you ads that show more Taylor specific information to you when you browse around their site on Saturdays. Another example could be if a server knows traffic from your IP address requests english speaking text or its IP geolocation comes from a predominantly english speaking country maybe the server wants to have the default language of the site to be in English. Most sites delete data and do not sell your information they collect though. Some websites have to follow certain State mandates and polices on cookie data. Most sites publish their privacy and cookie policy and give users the ability to opt in/out of analytics. Companies would pay big money for your analytics. Think of the value of knowing a list of people who are online looking to purchase certain products. How much would that list be worth to certain companies? What about a list of websites a person visits? How much would a list of IP addresses be if they were IP addresses known to be very rich people or people of power?

How to protect yourself
Some of the info you send like your IP address can be masked to help protect yourself. The way this is done is a virtual connection created between your device and a remote server, better known as a VPN server connection. There are many VPN servers you can subscribe to. Here is a list of "The Best VPN Services for 2024" according to PCmag.
Some important things to keep in mind
Your computer has an IP to get on the internet and that IP has a location
The VPN server has an IP to get on the internet and that IP has a location
Both your computer and the VPN server have different IP addresses which are at different locations
When you connect to a VPN and open your browser and load greg.heffner.live your computer will go through your VPN tunnel and use the VPN servers IP address to request the page instead of going through your local router. This way the webpage you are trying to view will log your VPN servers IP address instead of your own private IP address thus masking and protecting yourself. Not only is the connection protecting your IP address but the connection from your computer to the VPN server is encrypted so other devices on your network cant listen to your traffic as well. Well, they can listen to it but since its encrypted they wont be able to decipher what it is. This comes in handy when you use public wifi or connect to networks you dont trust or networks that have devices or people you dont trust on them. There is ways we can discuss in other blogs that people are able to "sniff" traffic to gather information about devices on the network. Encrypting your traffic allows you to protect your data and the information you send over the internet.
Public Wifi Safety Tips great read for people who use public networksRemote Connections
Another and probably the most used function of VPNs is the ability to use remote resources locally. Just like you able to connect to VPN servers that are publicly available to mask your IP as described before, there are private VPN servers that allow you to connect to remote devices or networks on the VPN servers local network. To say it another way you can connect your work computer at home to your work VPN so that you can access websites or applications as if you were in the office. This gives people the freedom to work in places that are convenient to them since traffic is encrypted and masked to the VPN servers network. Say you have a Pi-Hole server at home and you are trying to block ads when you are on vacation. Connect a VPN and route your traffic naturally to your home network with an encrypted tunnel from anywhere in the World.
Wrapping it up
I highly recommend you use a VPN for all of your online traffic. You never know what sites do with your info, you never know who is listening, and you never know where/when youre going to need to get to a certain file that you desperately need. In the age of Artificial Intelligence and Machine Learning any amount of information to build a profile of a persons habits, interests, or locations visited is a threat to your safety. Whether its to protect yourself from credit card fraud or to protect data integrity, VPNs help keep you safe.

Bing AI explanation of a VPN
Imagine a VPN as a secret tunnel for your computer when it goes online. When you use the internet with a VPN, it wraps your connection in a protective cloak.
Heres how it works:
Normal Internet: Without a VPN, your computer talks directly to websites. Its like walking outside without any walls around you. Anyone can see what youre doing!
With a VPN: When you turn on a VPN, its like stepping into a magical tunnel. Your internet traffic travels through this tunnel, and nobody outside can peek inside.
Privacy Magic: The VPN makes your computer look like its somewhere else (like a secret hideout). So, even if youre in Florida, it might seem like youre in New York!
Remember, a VPN keeps your online adventures private and safe!
About Me
I served in the U.S. Army, specializing in Network Switching Systems and was attached to a Patriot Missile System Battalion. After my deployment and Honorable discharge, I went to college in Jacksonville, FL for Computer Science. I have two beautiful and very intelligent daughters. I have more than 20 years professional IT experience. This page is made to learn and have fun. If its messed up, let me know. Im still learning :)